API Security & Management
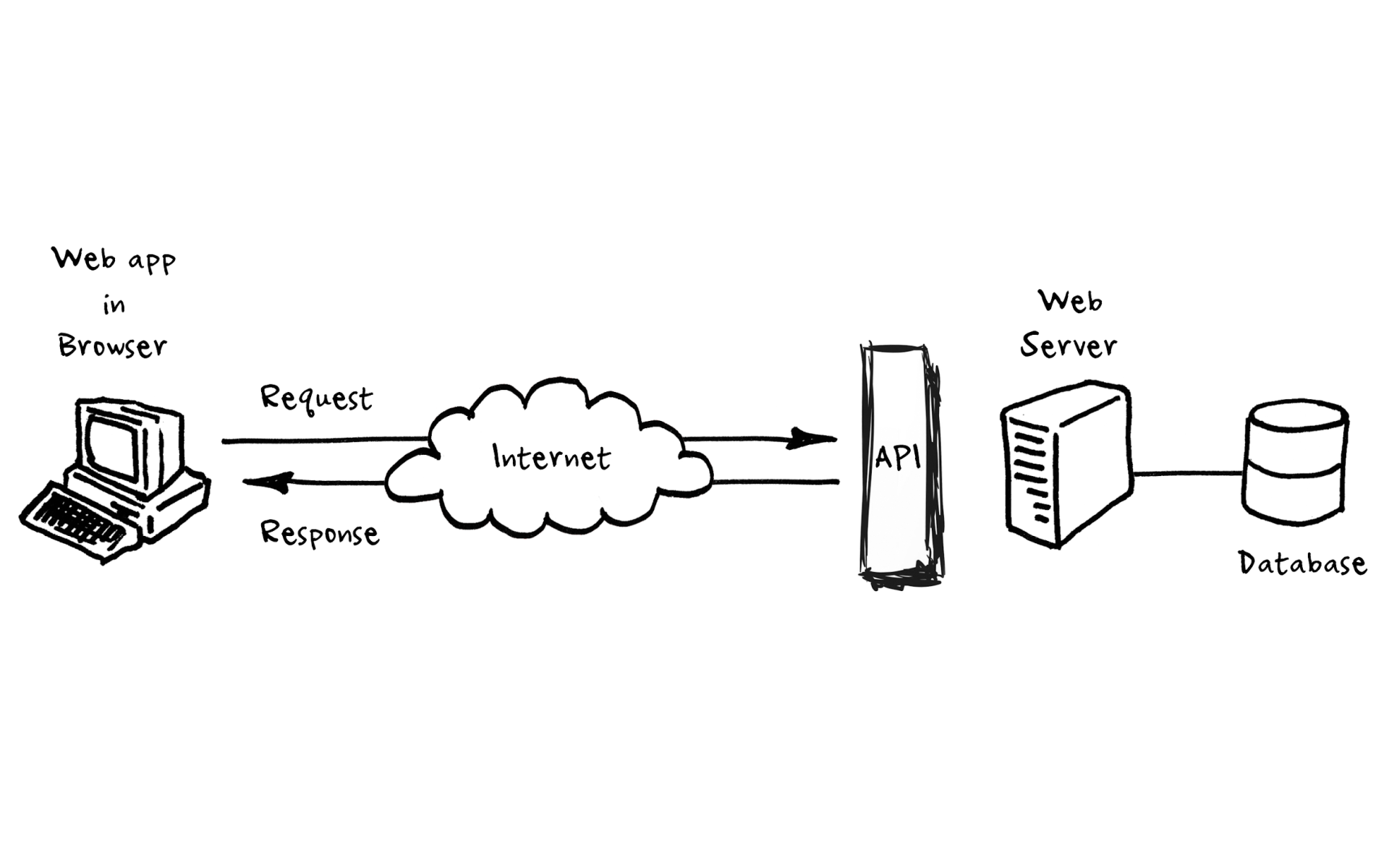
From a simple technical solution that allowed communication between applications, APIs have now become one of the engines of international innovation and business, and the most important tool of digital transformation. Be it banking services, marketplaces or mobile applications, their communication – and in part their security – always depends on APIs.
Challenges
Don’t downplay the danger lurking in your APIs
APIs have become increasingly the focus of attackers – almost every second company that uses APIs has had some kind of security incident connected to them. And thanks to the latest trends – such as microservices architecture – the number of APIs is growing exponentially, giving hackers an unprecedented size of attack surface.
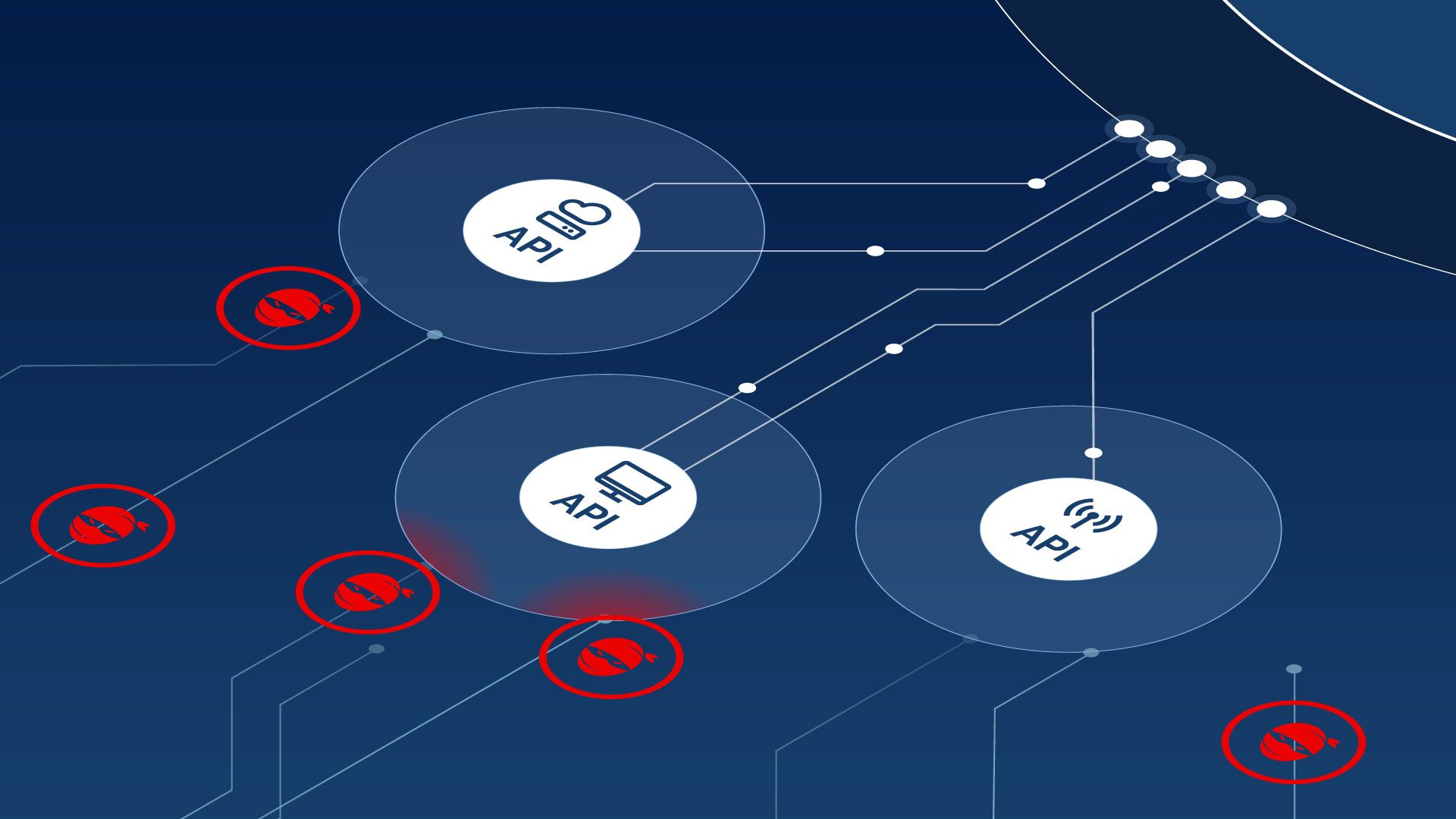
The latest threats are out of reach for traditional WAFs

When it comes to API security, relying solely on your Web Application Firewall gives you a false sense of security. Traditional WAFs are optimized for signature-based filtering of HTTP traffic. As a result, these WAFs cannot block targeted API attacks, as they are not optimized to fully understand the logic of API traffic.
You can't protect your API without a schema

An API schema identifies valid API requests and responses based on several parameters, not just the destination endpoint and the HTTP method. Without implementing API schemas, you cannot define what should happen in your API traffic. This can result in significant security risks for your business.
Internal APIs can go rogue

Designing and implementing the best functionality for your APIs may be much easier when you do it internally – business and development departments are much closer to each other. But even internal developers rarely give high priority to security, as businesses tend to focus on functionality, UX and deadlines. As security teams typically have limited influence on the development process, APIs may be vulnerable to multiple attack vectors.
OAuth is not enough

Yesterday’s defenses cannot protect against today's threats. The latest OWASP Top 10 list indicates that previously uncommon attacks have become widespread in the last few years – security based on authentication & authorization cannot protect you against these new threats. You need to validate your API traffic to ensure data flowing to and from API endpoints adheres to the specifications.
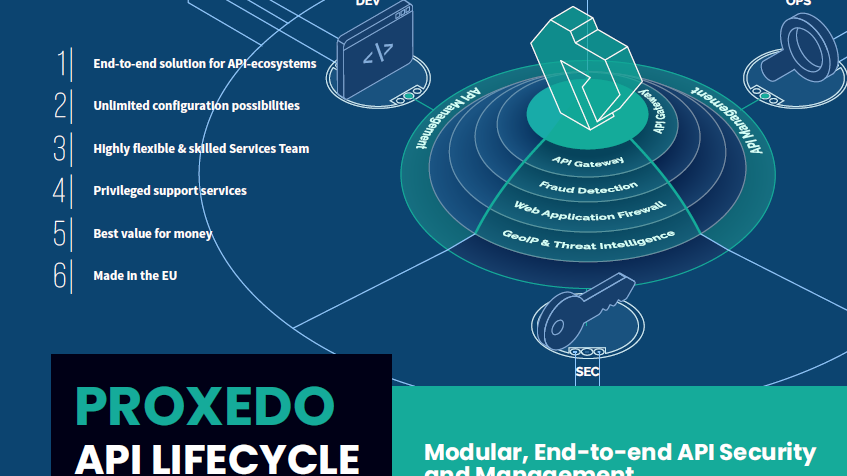
How we can help you
Only a holistic approach can fully protect your APIs
In addition to designing, developing, deploying, and monitoring APIs, our solution also ensures their security. It allows you to control the communication of your applications, monitor, encrypt and analyze your API traffic, prevent fraudulent financial transactions, and protect your web services by monitoring and filtering HTTP traffic.

API Management

Organizations need to manage and secure APIs during their entire lifecycle: design, deployment, monitoring, documentation, and publication. Our API management solution has a customizable portal that enables API consumers to fully engage with your business and manage your API lifecycle.
Web Application Firewall

A network firewall alone won’t protect your business from website attacks – we have developed our web application firewall to inspect and analyze the content of encrypted and unencrypted HTTP traffic and protect your web servers against APT (Advanced Persistent Threat) and other known attacks. This helps you mitigate the OWASP’s latest web application security risks, including injection and logging failures.
Fraud Detection

Losses from online financial fraud have been growing in recent years – battling against fraudulent transactions requires specialized tools. We use alternative data sources such as digital footprints to enable our automated machine learning algorithm to draw correlations and reports if certain transactions show suspicious signs. This approach reduces the cost, time lost, and challenges caused by fraud in online financial transactions.
Professional Services

The Balasys Professional Services team helps you design, deploy, and customize API solutions on-site. From simple start-up integrations to more complex projects, we offer a full range of services to ensure smooth deployment, from initial project scoping to post-integration support.